DNS Security Analysis Series: Part 2 - Malicious Domain Detection and Infrastructure Analysis
Advanced techniques for detecting malicious domains, analyzing domain characteristics, and identifying suspicious DNS infrastructure for security analysts.
Read Also
A deep dive into reverse engineering Go binaries. Learn about Go's internal data structures, compilation flags, PCLNTAB, ABI changes, and how to reconstruct slice and interface operations in IDA Pro.
The Chomsky Hierarchy and Security: Why Parsers Matter
A deep dive into formal language theory, automata, and Turing machines and their profound implications for cybersecurity. Learn why regex WAFs fail, how injection attacks exploit parser differentials, and how to apply grammar-based parsing to stealer logs and malware analysis.
Windows Development with C++: Part 1 - Foundations
Part 1 of the Windows Development series. Master Win32 API fundamentals, window creation, the message loop, and modern C++ patterns for native Windows programming.
Command & Control in 2025: Architecture, Evasion & Operations
A technical deep dive into modern C2 architecture (Sliver, Havoc), evasion techniques (Shellter Elite, Stack Spoofing, AMSI Blinding), and alternative infrastructure (Discord C2, Cloud Redirectors).
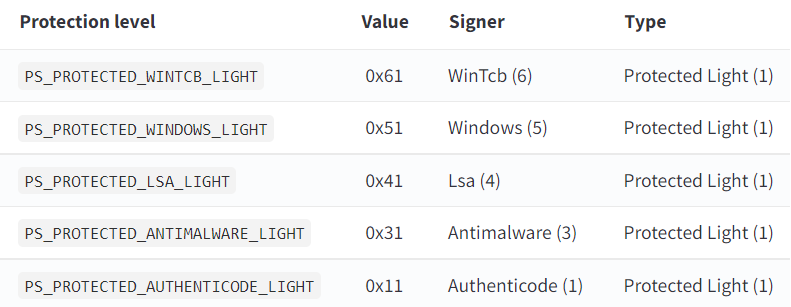
Part 1 of the Windows Protected Processes series. Learn about protected processes, Process Explorer limitations, and why even administrators can't access critical system processes like CSRSS and LSASS.
Advanced inspection techniques with Process Hacker, WinDbg kernel debugging, LSASS credential protection, BYOVD attacks, detection strategies, and system hardening for Windows protected processes.
DNS Security Analysis Series: Part 1 - DNS Fundamentals and Architecture
Deep dive into DNS architecture, record types, resolution process, and security analysis techniques for network defenders and DNS analysts.
Enterprise Network Architecture for Blue Team Operations: Visibility, Segmentation, and Modern Defense Strategies
A guide to enterprise network architecture for blue team operations.
Detection mechanisms, Windows processes, threads, memory types, and the Process Environment Block (PEB) for security professionals.
The Statistics You Learned in School but Never Applied
Bridge the gap between academic statistics and real-world engineering.