🎯 Blue Team Focus: This post explores network architecture from a defensive perspective, focusing on visibility, monitoring, and containment strategies essential for modern blue team operations.
Introduction
Knowing your network architecture is not just about knowing what cables plug to what other cables; it's the beginning of gaining a defensive advantage. For professionals working in blue team roles, network architecture has a profound impact on the ability to detect threats, respond to incidents, and contain an attacker to help ensure they do not accomplish their objectives.
Today's enterprise networks are broad and convoluted, consisting of routers, switches, firewalls, and numerous other and security devices. Each of these devices can contribute positively to your defensive posture or introduce blind spots in your defenses that can be utilized by an attacker. This article examines how to conduct network architecture that will improve your capacity to monitor your network for anomalies and a strategy for containment when under attack.
The Evolution from Home to Enterprise Networks
Deconstructing the Home Router
To understand enterprise network complexity, let's start with something familiar: your home router. That single device actually performs multiple critical functions:
Home Router = Firewall + Router + Switch + Access Point
Behind the scenes, your home router contains:
- 2-port Firewall: Blocks inbound traffic from the internet
- 2-port Router: Routes traffic between your LAN and the internet
- Unmanaged Switch: Connects multiple wired devices
- Wireless Access Point: Provides WiFi connectivity
This all-in-one approach works for home networks with minimal security requirements, but enterprises need granular control over each function.
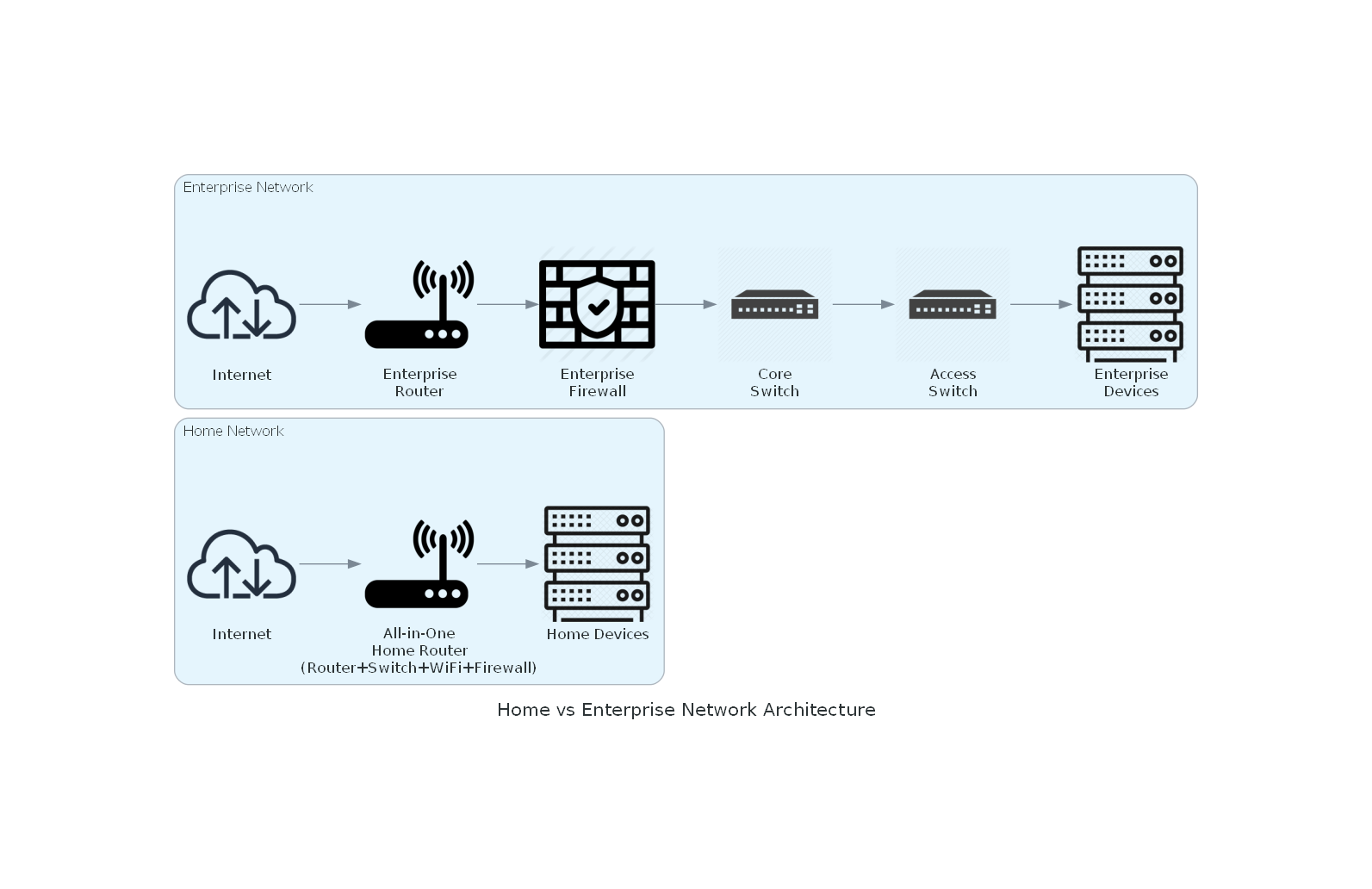
This comparison helps demonstrate the essential differences between home and enterprise network architecture. While home networks merge several functions into one device, enterprise networks distribute functions into discrete, specialized elements, ensuring appropriate security, scalable growth, and individual controls within their networks.
Enterprise Network Separation
Enterprise networks separate these functions into dedicated devices for several critical reasons:
Scalability: Enterprise routers handle multiple subnets and hundreds of network segments, not just "inside" and "outside."
Security: Dedicated firewalls provide deep packet inspection, application-layer filtering, and advanced threat detection.
Visibility: Managed switches offer traffic mirroring, NetFlow generation, and detailed monitoring capabilities.
Redundancy: Critical network functions can't depend on a single device—enterprise networks require multiple layers of redundancy.
Network Zones: The Foundation of Defense
Understanding Network Segmentation
Network zones are the cornerstone of enterprise security architecture. Instead of a flat network where any device can communicate with any other device, zones create security boundaries that limit blast radius and slow attacker movement.
Common Enterprise Zones:
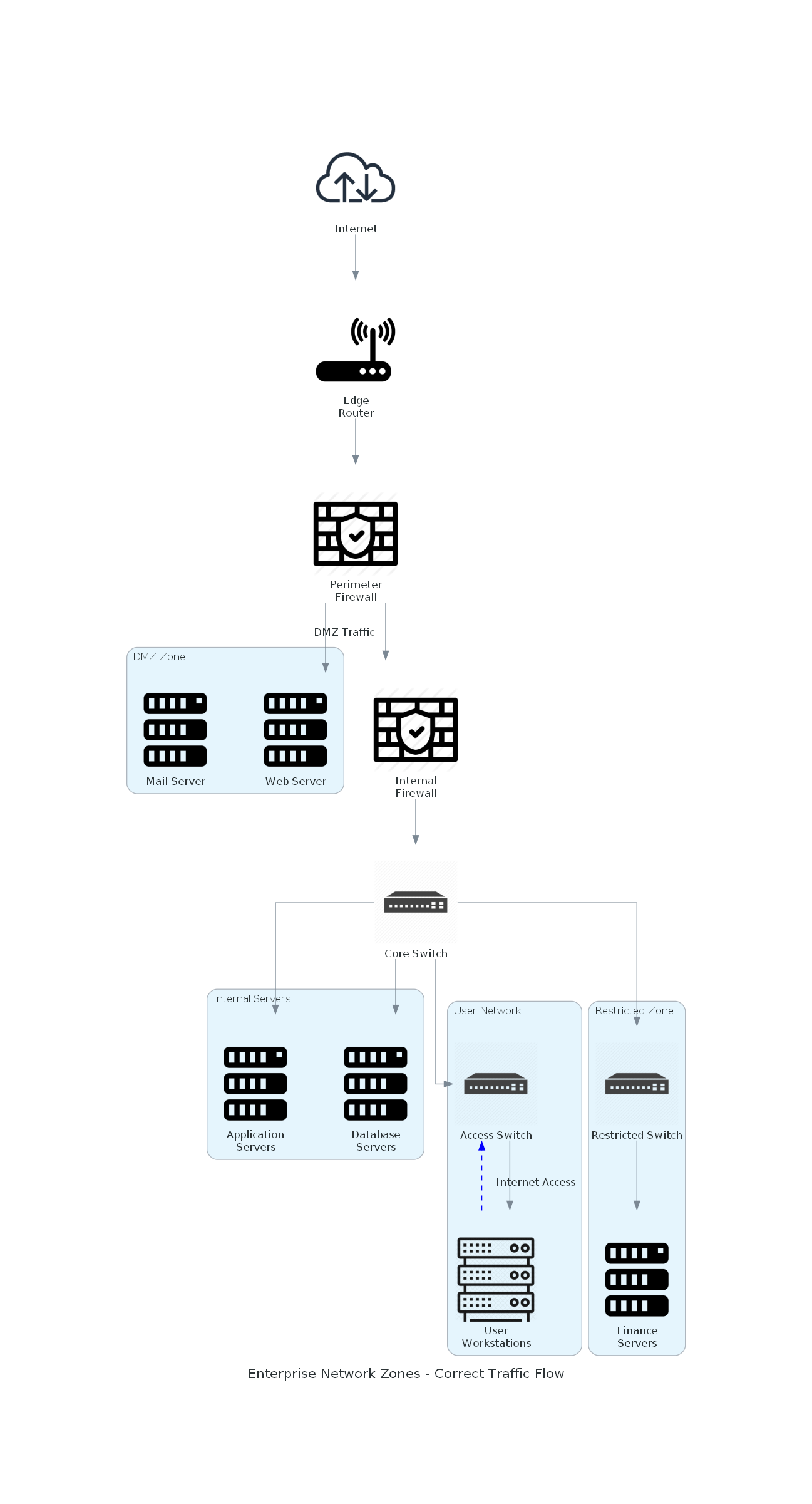
This diagram demonstrates the proper flow of network traffic in an enterprise. You can see that user devices connect through access switches to the core of the network. Internet access flows through the edge router and the perimeter firewall. This is how a real-world network ideally would be laid out. Network traffic goes in and out through proper network devices and not random magical connections.
Zone-Based Traffic Flow Rules
Effective network segmentation isn't just about creating zones—it's about controlling traffic flow between them. Here's an example enterprise firewall ruleset:
| Traffic From → To | WAN | DMZ | IoT | Users | Servers | Restricted |
|---|---|---|---|---|---|---|
| WAN | N/A | Allowed | Blocked | Blocked | Blocked | Blocked |
| DMZ | Blocked | Partial | Blocked | Blocked | Blocked | Blocked |
| IoT | Allowed | Blocked | Allowed | Blocked | Blocked | Blocked |
| Users | Proxy Only | Allowed | Allowed | Partial | Allowed | Partial |
| Servers | Blocked | Blocked | Blocked | Blocked | Partial | Blocked |
| Restricted | Blocked | Blocked | Blocked | Blocked | Blocked | Partial |
This ruleset demonstrates several key security principles:
- Internet traffic can only reach DMZ services
- IoT devices are isolated from internal resources
- Servers cannot initiate outbound connections (preventing data exfiltration)
- User devices have controlled access based on business needs
Enterprise Network Components: A Blue Team Perspective
Managed Switches: Your Traffic Visibility Foundation
Unlike home network switches, enterprise managed switches provide critical capabilities for blue team operations:
Network Flow Visibility: Generate NetFlow records showing source, destination, ports, and traffic volumes for every conversation.
Mirror (SPAN) Ports: Copy all traffic from specific ports or VLANs to monitoring devices for deep packet inspection.
Access Control Lists (ACLs): Implement device-level isolation to prevent lateral movement within the same VLAN.
Virtual LANs (VLANs): Logically separate traffic on the same physical infrastructure.
The VLAN Challenge: Physical vs. Logical Networks
VLANs add complexity that blue teams must understand to properly monitor networks:
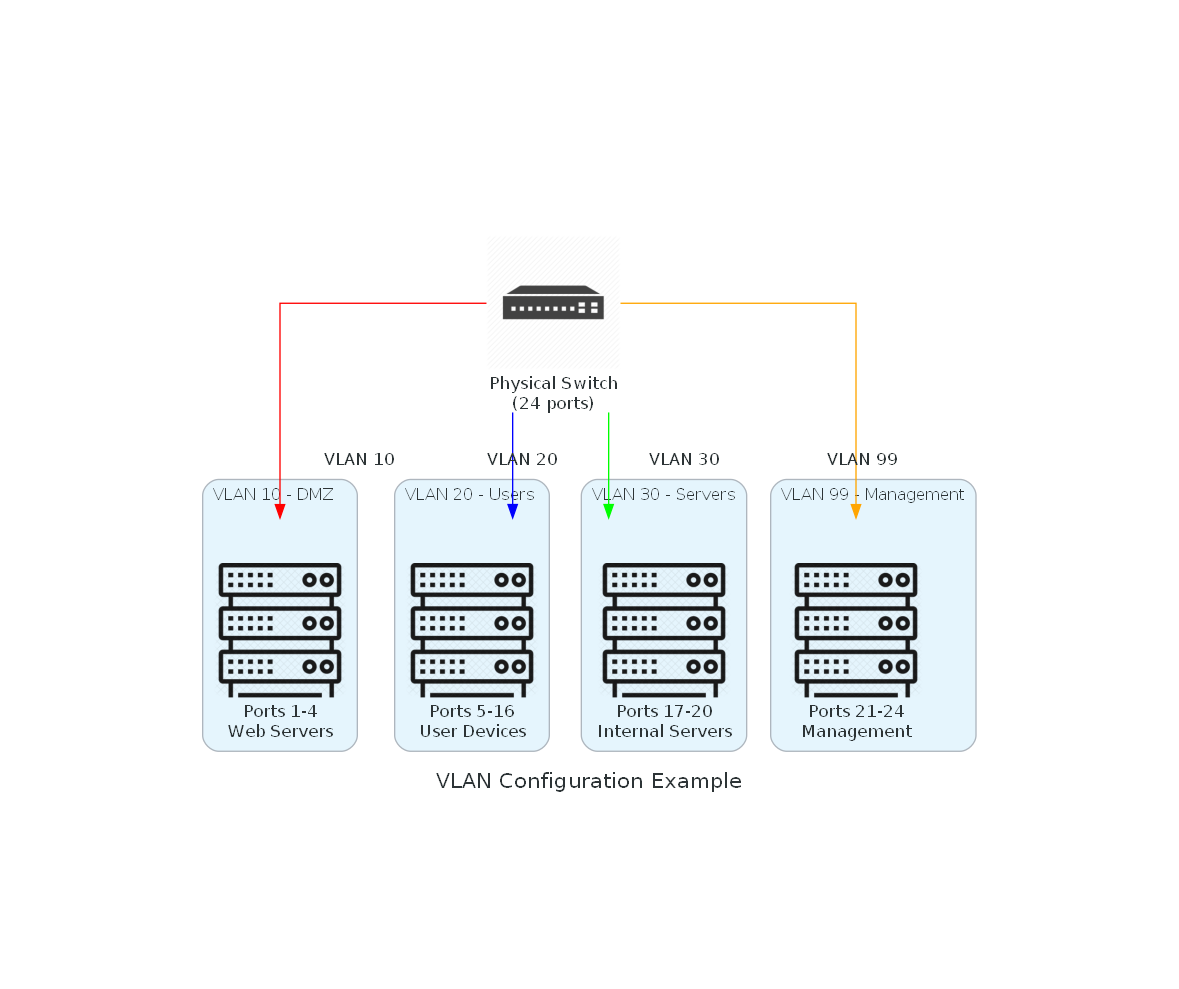
This diagram shows how a single physical switch can be logically divided into multiple VLANs, with different ports assigned to different network segments. This is how enterprises create network isolation without requiring separate physical switches for each network zone.
Critical Implication: To determine what subnet a device is on, you must know both the physical port AND the VLAN configuration. This affects:
- Incident Response: Where to look for traffic captures
- Lateral Movement Detection: Understanding possible attack paths
- Forensic Analysis: Reconstructing attacker movement
Enterprise Firewalls: Next-Generation Capabilities
Modern enterprise firewalls go far beyond simple port-based filtering:
Layer 7 Application Control: Identify and control applications regardless of port:
Traditional Firewall: Block port 22 (SSH)
Next-Gen Firewall: Allow SSH for IT staff only, block for everyone else
User Identity Integration: Make decisions based on user identity, not just source IP:
Rule Examples:
- Sally (IT): SSH allowed to server VLAN
- Bob (Accounting): FTP allowed to finance servers only
- Manufacturing VLAN: No internet access
- Executives: Social media allowed (if necessary)
Deep Packet Inspection: Analyze traffic content to detect threats and policy violations:
- Detect SSH tunneling over HTTP
- Identify cryptocurrency mining traffic
- Block specific file types regardless of protocol
- Prevent data exfiltration via DNS tunneling
Traffic Visibility: The Blue Team's Eyes and Ears
Understanding Network Monitoring Technologies
Before deploying network monitoring solutions, it's essential to understand the two primary methods for capturing network traffic: Network Taps and Mirror Ports.
Network Taps (Test Access Points)
Network taps are physical hardware devices that provide a permanent, dedicated connection for monitoring network traffic. They sit directly in the network path between two devices (like between a switch and router) and create copies of all passing traffic.
How Network Taps Work: Network taps get injected in the network by being installed inline between network devices, allowing the capture of some / all traffic flowing through the point of connection. Being considered passive monitoring devices that simply make copies of traffic, they do not affect the performance of the network. They operate on traffic from both directions, capturing full duplex exchanges (or bidirectional) simultaneously. The most valuable feature of network taps is that they introduce no latency or packet loss on the monitored links, presenting no impact on production network performance on paper.
Main Characteristics:
- Dedicated hardware device for traffic monitoring
- Requires physical installation and network downtime
- Provides complete traffic visibility for the monitored link
- Cannot selectively monitor specific VLANs or ports
Mirror Ports (SPAN Ports)
Mirror ports, also called SPAN (Switch Port Analyzer) ports, are switch features that copy traffic from one or more source ports to a designated monitoring port. This is a software-based approach built into managed switches.
How Mirror Ports Work: Mirror ports work by using software configuration through the switch management interface. The interface gives the administrator the ability to establish a port mirroring capability that copies traffic from a designated source port that will be monitored directly to a destination monitoring port. In addition to basic traffic monitoring, mirror ports provide flexible selection options to monitor specific ports, VLANs or specific traffic types depending on their security needs. More sophisticated switches include the option for remote mirroring, utilizing a network protocol to accomplish this and are labeled as RSPAN (Remote SPAN) and ERSPAN (Encapsulated Remote SPAN) to monitor distributed across multiple segments of the network.
Main Characteristics:
- Built-in feature of managed switches
- No additional hardware required
- Configurable via switch CLI or web interface
- Can introduce packet loss under high traffic loads
Cisco SPAN Configuration Examples:
! Basic Local SPAN - Mirror single port to monitoring port
monitor session 1 source interface GigabitEthernet0/1
monitor session 1 destination interface GigabitEthernet0/24
! Mirror multiple ports to single destination
monitor session 2 source interface GigabitEthernet0/1 - 10
monitor session 2 destination interface GigabitEthernet0/24
! Mirror specific VLAN traffic
monitor session 3 source vlan 100
monitor session 3 destination interface GigabitEthernet0/24
! Mirror both ingress and egress (default is both)
monitor session 4 source interface GigabitEthernet0/1 both
monitor session 4 destination interface GigabitEthernet0/24
! Mirror only ingress traffic
monitor session 5 source interface GigabitEthernet0/1 rx
monitor session 5 destination interface GigabitEthernet0/24
! Remote SPAN (RSPAN) - Mirror traffic to remote switch
vlan 999
remote-span
!
monitor session 6 source interface GigabitEthernet0/1
monitor session 6 destination remote vlan 999
! Encapsulated Remote SPAN (ERSPAN) - Mirror over IP network
monitor session 7 type erspan-source
source interface GigabitEthernet0/1
destination
erspan-id 1
ip address 192.168.1.100
origin ip address 192.168.1.1
! View current SPAN sessions
show monitor session all
show monitor session 1 detail
SPAN Session Limitations:
- Maximum Sessions: Most Cisco switches support 2-4 local SPAN sessions
- Destination Ports: Cannot be source ports in other sessions
- Bandwidth: Destination port must handle aggregated source traffic
- Packet Loss: May occur during high traffic periods
Network Tap vs. Mirror Port Decision Matrix
Choosing between network taps and mirror ports significantly impacts your monitoring capabilities:
| Capability | Network Tap | Mirror Port |
|---|---|---|
| Lateral Movement Detection | Limited+ | Excellent |
| Bandwidth Handling | Excellent | Limited++ |
| Device Impact | None | CPU overhead |
| VLAN Tag Preservation | Yes | Sometimes lost |
| Cost | Higher | Lower |
| Deployment Complexity | Higher | Lower |
+ Network taps miss intra-subnet traffic that doesn't traverse upstream devices ++ Mirror ports can drop packets when aggregating full-duplex traffic
Strategic Placement for Maximum Visibility
Critical Monitoring Points:
- Perimeter Ingress/Egress: Monitor all traffic entering and leaving your network
- Inter-Zone Boundaries: Place sensors between major network segments
- Critical Asset Access Points: Monitor access to crown jewels and sensitive systems
- Internal Chokepoints: Capture traffic at network convergence points
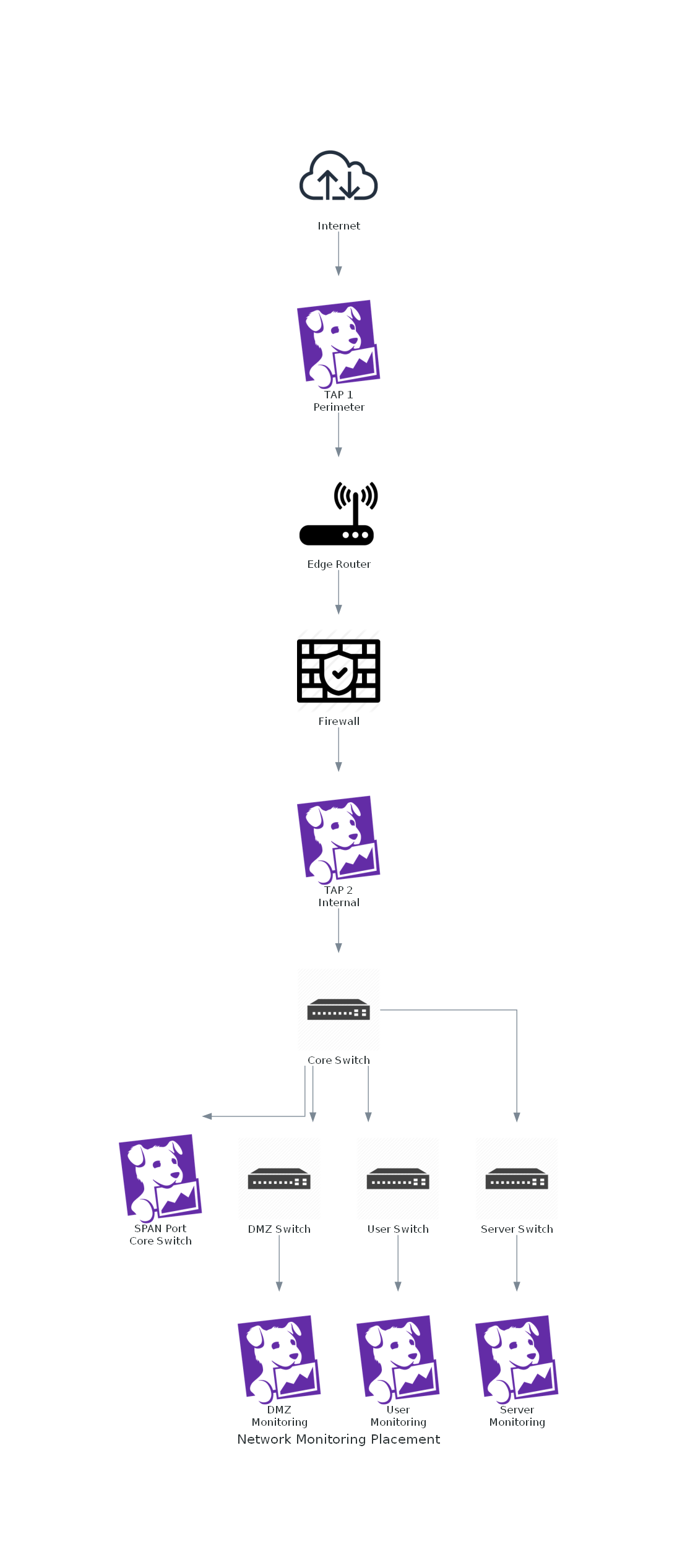
This illustration shows optimal layered deployment of monitoring tools (TAPs and SPAN ports) in order to obtain the best possible visibility across different segments of the network, with the least amount of blind spots.
The Zero Trust Evolution
From Perimeter Defense to Asset-Centric Security
Traditional network security relied on strong perimeters with soft interiors. The zero trust model assumes breach is inevitable and focuses on asset-centric protection:
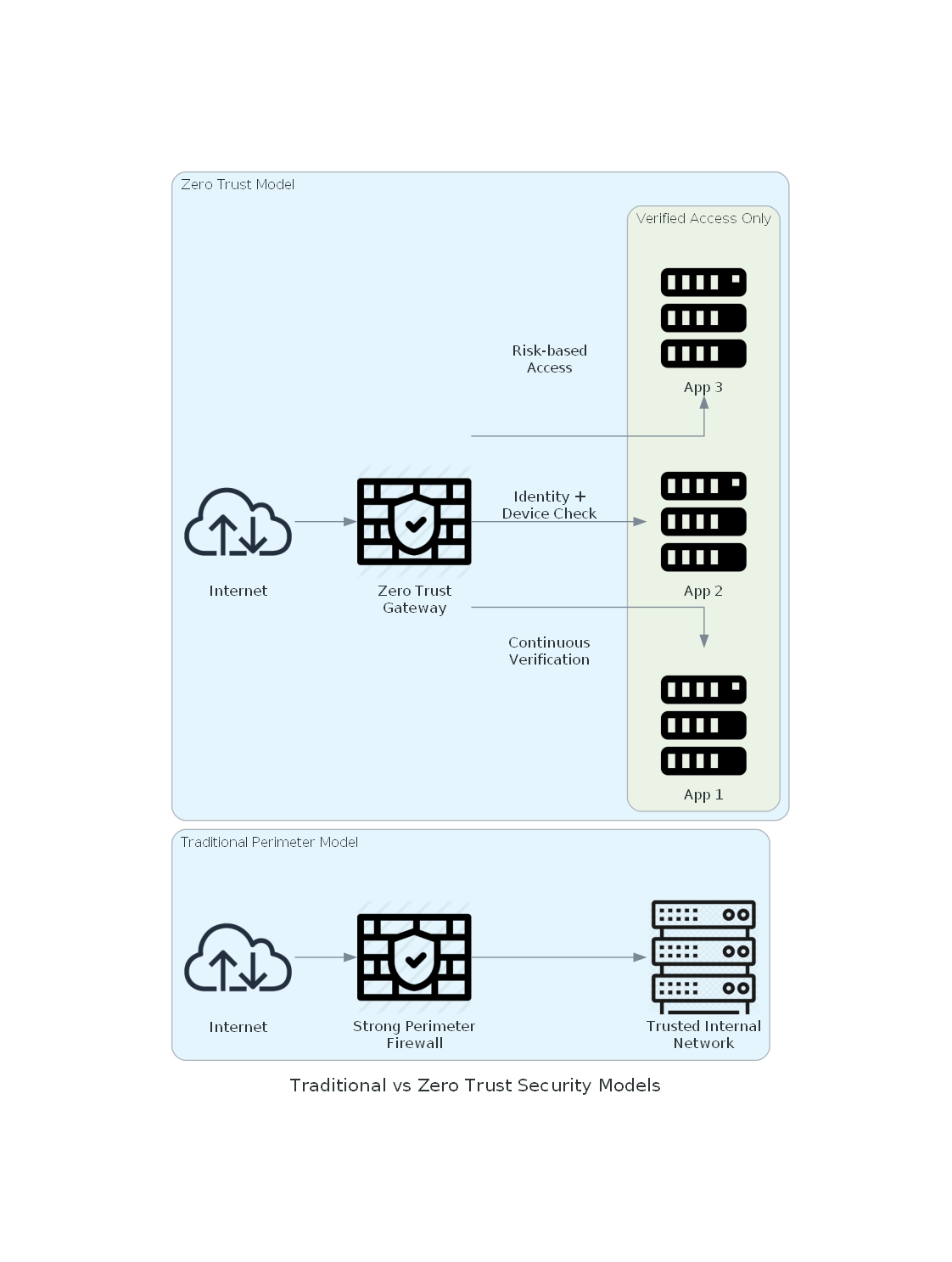
This diagram shows the evolution from traditional perimeter-based security (strong firewall with trusted internal network) to zero trust architecture (where every access request is verified regardless of location).
Zero Trust Principles for Blue Teams:
- Assume Hostile Network: Treat all network traffic as potentially malicious
- Verify Everything: Authenticate and authorize every connection
- Least Privilege Access: Grant minimal necessary permissions
- Dynamic Policy Enforcement: Adjust security posture based on risk indicators
- Continuous Monitoring: Never stop validating trust assumptions
Real-World Zero Trust Implementation: Google's BeyondCorp
Google's BeyondCorp is a zero trust security model that Google created and then deployed internally to transition away from traditional VPN-based remote access in their organization. Google initiated the BeyondCorp project in response to the 2009 Operation Aurora cyberattacks, which exposed the limitations of perimeter-based security. BeyondCorp re-considers how employees access and utilize corporate applications and data. Rather than using network location as a proxy for trust, BeyondCorp treats all networks as untrusted, and access to corporate resources is made based on device and user identity, device security posture, and application sensitivity.
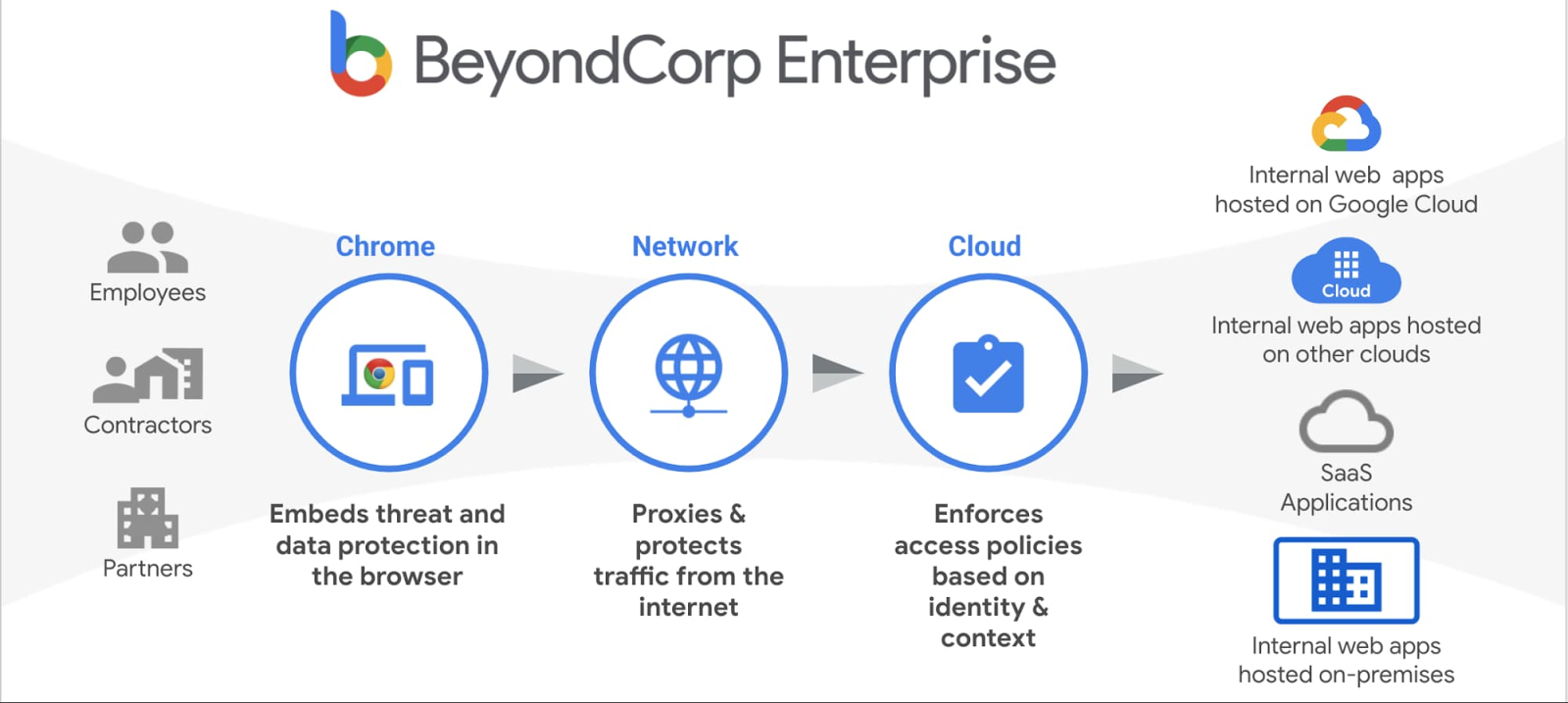 Google Cloud Zero Trust BeyondCorp Enterprise
Google Cloud Zero Trust BeyondCorp Enterprise
The BeyondCorp model deconstructs the traditional corporate perimeter, enforcing access controls based on continuous verification of user and device context rather than network location and enables employees to work in any location securely without a VPN connection. This has been incredibly useful for increasingly common dispersed workforces and cloud-first organizations.
Google's BeyondCorp demonstrates practical zero trust implementation:
- No VPN Required: Users access resources directly from any network
- Device and User Verification: Multi-factor authentication and device certificates
- Application-Level Access: Granular permissions for specific applications
- Continuous Risk Assessment: Access decisions based on current risk profile
Defending Against Modern Threats
The WannaCry and NotPetya Lessons
The 2017 WannaCry and NotPetya outbreaks demonstrated the critical importance of network segmentation:
Attack Pattern:
- Initial compromise via phishing or drive-by download
- Exploitation using NSA's ETERNALBLUE (MS17-010)
- Rapid lateral movement across flat networks
- Company-wide outages within hours
Segmented Networks: Slower, contained spread Flat Networks: Catastrophic organization-wide failure
Defending Flat Networks
If you inherit a flat network, focus on these compensating controls:
Host-Based Defense:
- Endpoint Detection and Response (EDR) on all systems
- Host-based firewalls with strict rules
- Anti-exploitation tools (Windows Defender Exploit Guard)
- Application whitelisting where possible
Enhanced Monitoring:
- Comprehensive NetFlow collection
- Deep packet inspection at key points
- Behavioral analytics to detect lateral movement
- Rapid incident response procedures
Network Micro-Segmentation:
- Software-defined perimeters
- Container and VM isolation
- Application-layer segmentation
- Identity-based access controls
Practical Implementation Guide
Network Asset & Configuration Documentation
Track devices, IP addresses, ports, VLANs, connections, and more.
| Tool | Features | Notes |
|---|---|---|
| NetBox | IPAM, DCIM, rack layout, cable paths | Open-source, widely adopted |
| phpIPAM | IP address management, VLANs, VRFs | Lightweight and web-based |
| Ralph | Asset lifecycle management + discovery | Inventory-focused, open-source |
| Device42 | Comprehensive network, server, and software asset mapping | Paid, enterprise-grade |
| GLPI + FusionInventory | IT asset mgmt + auto-discovery | Open-source combo used in large orgs |
Building Your Network Diagram
Every blue team needs a current network diagram showing:
Physical Components:
- Router and switch locations
- Firewall placement and rule summaries
- Network tap and mirror port locations
- Critical server and service locations
Logical Layout:
- VLAN configurations and purposes
- Traffic flow patterns between zones
- ACL and firewall rule summaries
- Monitoring coverage maps
Monitoring Strategy Development
Immediate Actions: Start your monitoring strategy with a full inventory of every networked device, documenting each router, switch, and firewall in your environment. Next, lay out traffic flows to understand how data moves between the different zones of your network, which is crucial to knowing how to design solid monitoring placement. Locate the blind spots where you currently do not have monitoring, paying particular attention to areas where attackers would have lateral movement capabilities but without monitoring service. Ultimately, your monitoring visibility efforts will be sponsored by understanding your respective crown jewels and what paths lead to the most critical of your assets.
Long-Term Improvements: Gradually implement zero trust principles throughout your network architecture, systematically reducing implicit trust relationships that attackers can exploit. Enhance segmentation by adding granular controls between systems, creating smaller security boundaries that limit the blast radius of potential breaches. Build automated response capabilities that can contain threats without human intervention, reducing the time between detection and containment. Establish a continuous assessment program that regularly tests and improves your defenses, ensuring they evolve alongside emerging threats and changing network architecture.
Don't forget that solid network monitoring is not just a set-it-and-forget-it deployment. It is a constantly evolving process that should adapt to your network architecture and landscape of threats. Start monitoring with a focus on the areas of highest risk and those that are most critical, then gradually expand your monitoring to cover more ground. All the while covering the risk areas we discussed earlier, the goal is to eventually have layers of visibility that overlap within the network that in turn provide great coverage and reasonable alert volumes. As your network grows and changes, your monitoring systems should continually be tested and tuned!
Conclusion
Network architecture forms the foundation of effective blue team operations. Without understanding your network's physical layout, logical configuration, and traffic flows, you cannot effectively monitor for threats or respond to incidents.
Modern attacks move fast; WannaCry and NotPetya demonstrated that flat networks can be compromised organization-wide within hours. By implementing proper network architecture principles, blue teams can detect threats earlier, respond faster, and minimize the impact of successful breaches.
Additional Resources
Network Security Design:
- NIST Cybersecurity Framework - Comprehensive security guidelines
- SANS Network Forensics - SANS FOR572 resources list
- Zero Trust Architecture - NIST guidance on zero trust implementation
Network Monitoring Tools:
- Wireshark - Network packet analysis
- Zeek (formerly Bro) - Network security monitoring platform
- Suricata - Intrusion detection and prevention
- SiLK - Network flow analysis suite
Blue Team Resources:
- MITRE ATT&CK - Adversary tactics and techniques
- Blue Team Handbook - Incident response procedures
- SANS Blue Team Operations - Professional training course
Remember: The best network defense is one that assumes compromise has already occurred. Design your architecture to detect, contain, and respond to threats—not just prevent them.